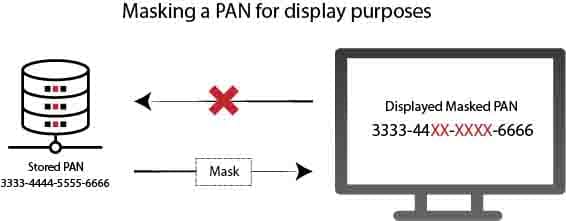
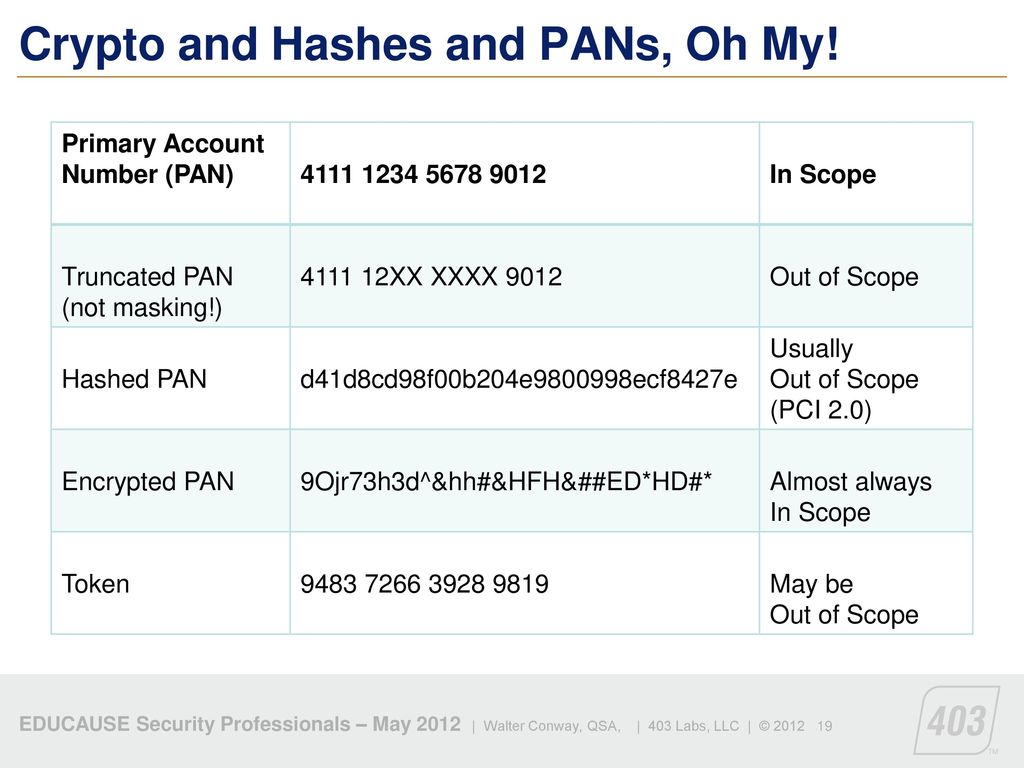
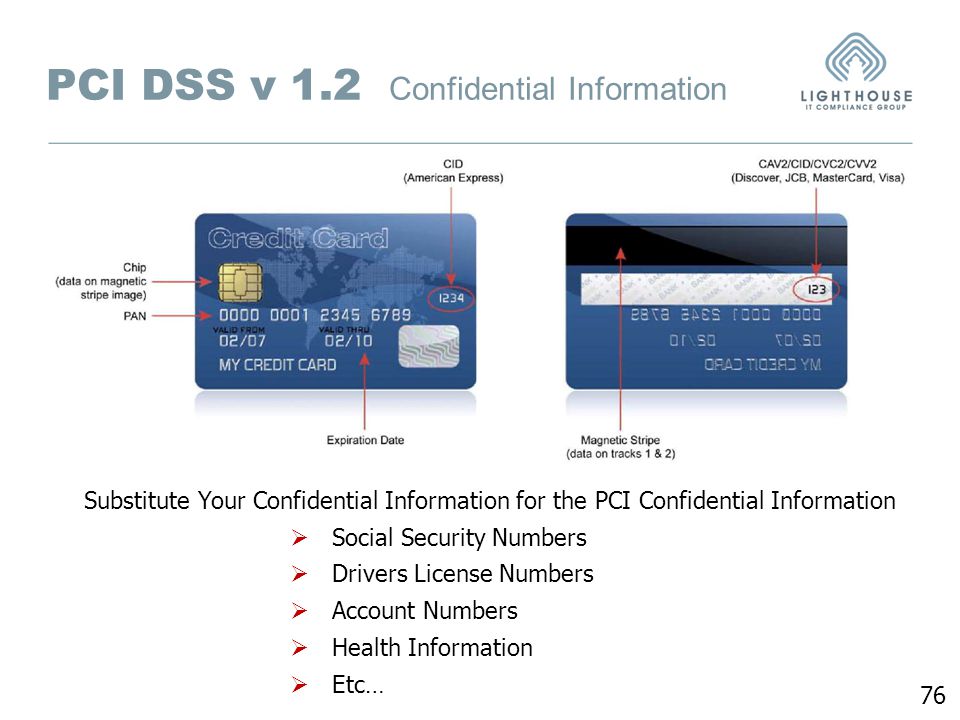
pci dss - I have recovered my credit card PAN (6 chars masked) and expiration date on a merchant site, acceptable or not? - Information Security Stack Exchange

pci dss - I have recovered my credit card PAN (6 chars masked) and expiration date on a merchant site, acceptable or not? - Information Security Stack Exchange

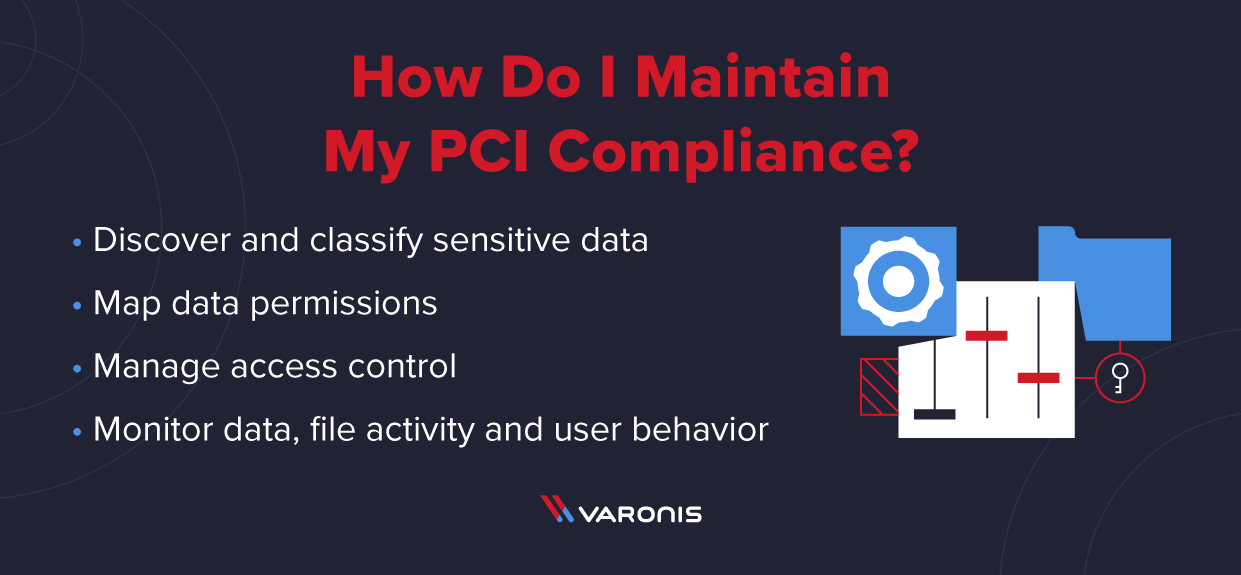
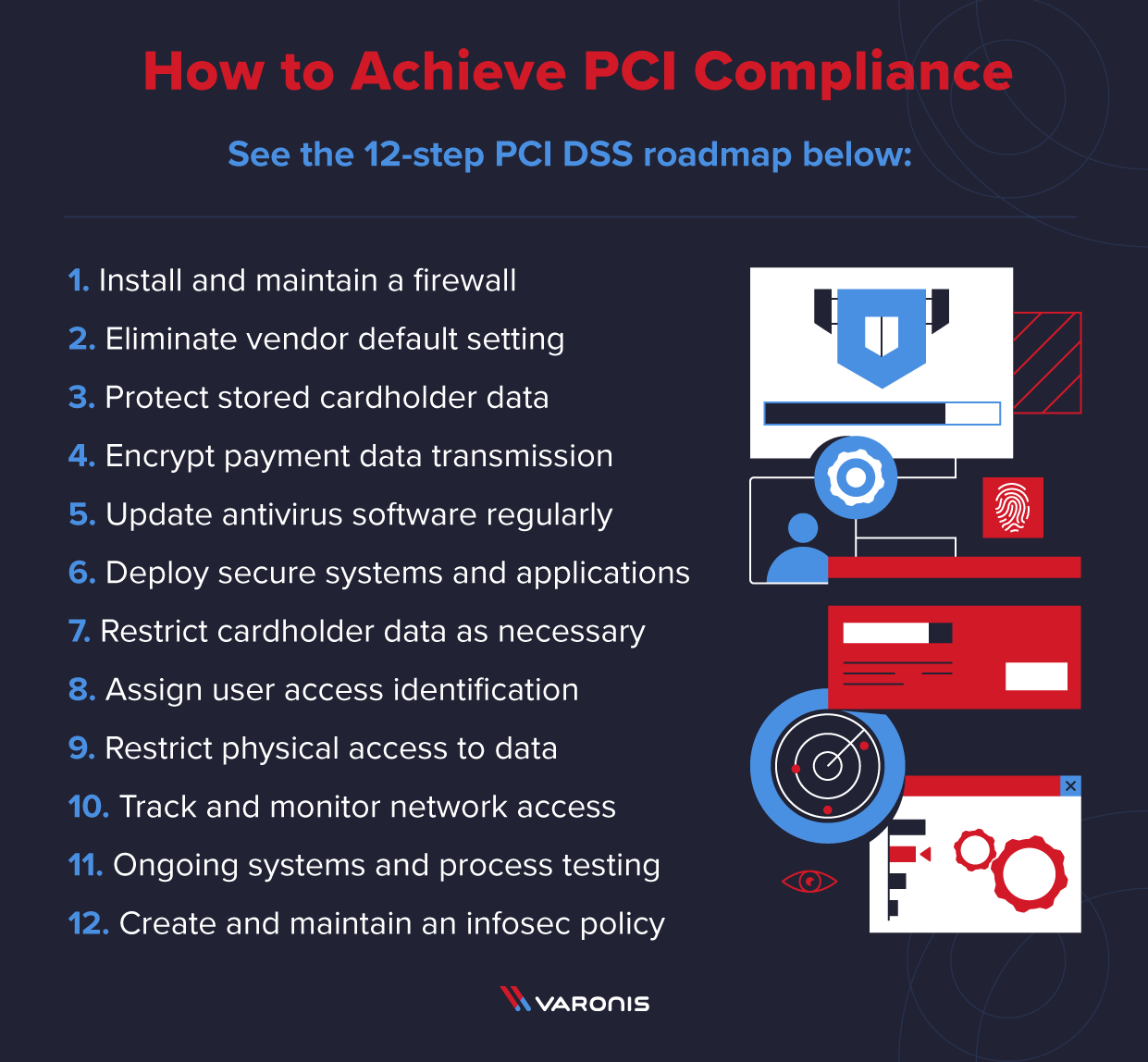
Implement the 12 best practices of PCI-DSS security compliance within your organization? | by Mr.Vic | Nerd For Tech | Medium

Musings on Information Security and Data Privacy: PCI Compliance, Security in isolated System and Parking Tellers (2nd)